
Using a Six Sigma Approach for Heightened Cybersecurity
Lately, cybersecurity has been at the forefront of many blogs and forums around cybersecurity. From spear-phishing email attacks at the White House to national cyber-attacks, frequently blamed on China, North Korea, and Russia.
Fortunately, many organizations have recognized this and are now putting dedicated cyber security teams in place. These teams can sometimes be referred to as “Red Teams”.
The blessing and curse of Six Sigma is that most people believe that you must have a background in statistics. While basic statistics are taught to Six Sigma Green Belts, many tools are available that mistake-proof things, like processes, outputs, and you get the drift. Remember, Six Sigma solves a practical problem by converting it to a statistical problem, then developing a statistical solution, which is finally turned into a practical solution.
The Six Sigma DMAIC approach can fit resoundingly like a glove with cybersecurity’s Identify-Protect-Detect-Respond methodology. If you want to know more about cybersecurity, I suggest you have a look at standards such as ISO 27001 – Information security management systems, ISO 27002 – Security techniques – Code of practice for information security controls, and ISO 27018 – Security techniques – Code of practice for protection of personally identifiable information (PII) in public clouds, which are the framework for any Information Security Management System (ISMS).
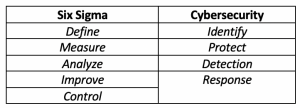
Now back to Six Sigma and Cybersecurity. Below is comparative methodology table. At the end of this article you’ll find a leak to download templatestaff’s daily cybersecurity checklist for enterprise settings.
You’ll see that the two approaches map out almost identically, fitting like a proverbial glove. Don’t get too excited about trying to imagine the cybersecurity map looking similarly like a Six Sigma approach. There’s nothing new here. Both remind me of Deming’s Plan-Do-Check-Act cycle, which can be traced as far back as 1959.
Identify
Identify the needs. Evaluate the business systems your organization depends on. Some offices could go 24 hours without a fax machine or longer. Email outages of several hours may be acceptable, however, to others, it may not be acceptable at all.
Who are the users? Will everyone be using the company’s email? Will some users have company supplied mobile devices? Would there be iPhones or Android type devices?
These are some of the questions every IT administrator must now begin to ask and strive to stay on top of.
Protect
This activity ensures you’ve covered all aspects. For instance, do you have a firewall in place to protect your server infrastructure from the outside world’s hacks and attempts and penetration?
Have all end-points been protected? This includes laptops, desktop computers, mobile phones (read more about MDM – mobile device management), managed switches, tablets, and other IP appliances that offer you a secure (https) or non-secure (http) website to access its configuration, or back-end.
What end-point protection tool are you using and have you evaluated the different benefits for each? For example, have you determined whether to use Sophos or Carbon Black? A Pugh Matrix can definitely help with any decision-making.
Here’s a case in point. We want to protect the company’s computer fleet (includes laptops, desktops, and tablets) from being the point of entry in terms of data theft. That’s right, we don’t want anyone to insert a USB key and copy files from the computer to be transferred to another situated outside the company’s premises, or worse, on a competitor’s computer. So we lock it down. Sure, this can be painful and have people worried that their employer is playing big brother, but when you weigh this in the balance of having critical intellectual property (IP) theft, many organizations will invest slightly in human resources (HR) to promote a culture of security awareness.
Detection
In Protect, we explored end-point protection and the need to install end-point protection, sometimes also called an intrusion detection system (IDS).
Advanced email threat systems such as Barracuda, Mimecast, and Sophos use algorithms and machine-learning to monitor the behaviour of the user or other system agents. This is done by learning the user’s normal behaviour than monitoring for whether different file servers or files or resources were located, accessed, and even downloaded.
Back to the previous case in point, the USB key. The moment the key is connected to the one of the computer’s USB ports, it becomes “detected” and here we see how some of the elements of the IT Security Response Plan (Identify, Protect, Detect, Response) may overlap.
Response
The response phase is no less important than the previous ones. Much of the response plan here means training. It means administrator training, new hacking techniques that bring social hacking to a new level. It especially means end user training. Your users should be trained on how to recognize bad links or phishing scams. At best, they should be conditioned to immediately notify IT personnel if in doubt.
Should an IT security incident occur I don’t need to tell you that the quicker the response plan has been executed, the lower the chance of a widespread propagation of the malware or virus in the first place.
In terms of response, always be sure to send a note out to the company explaining what happened and what measures have been put in place to prevent an incident like this from reoccurring.
Download the [Download not found] here


Be the first to comment